Configure Dynamic Lock
Users with smartphones can take advantage of a feature introduced with the Creators Update for Windows 10 Version 1703, which allows users to automatically lock their devices whenever they’re not using them. (At the time of this writing, iPhone devices do not support this feature.)
This feature relies on a Bluetooth link between your PC and paired smartphone.
To configure Windows 10 Dynamic Lock, use the following steps:
- Open the Settings app and select Accounts.
- Select Sign-in options and scroll to Dynamic lock.
- Select the Allow Windows to lock your device automatically when you’re away check box.
- Select the Bluetooth & other devices link.
- Add your smartphone using Bluetooth and pair it.
- Return to the Dynamic lock page, and you should see your connected phone.
- Your device will be automatically locked whenever Windows detects that your connected smartphone has moved away from your desk for 30 seconds.
You can configure Dynamic Lock functionality for your devices using the Configure Dynamic Lock Factors GPO setting. You can locate the policy setting at Computer Configuration > Administrative Templates > Windows Components > Windows Hello for Business.
Configure VPN client
In Windows 10, you can create a VPN that enables data to be transferred through a virtual private network using a secured connection (known as a tunnel) over a public network, like the internet, as displayed in Figure 1-21.
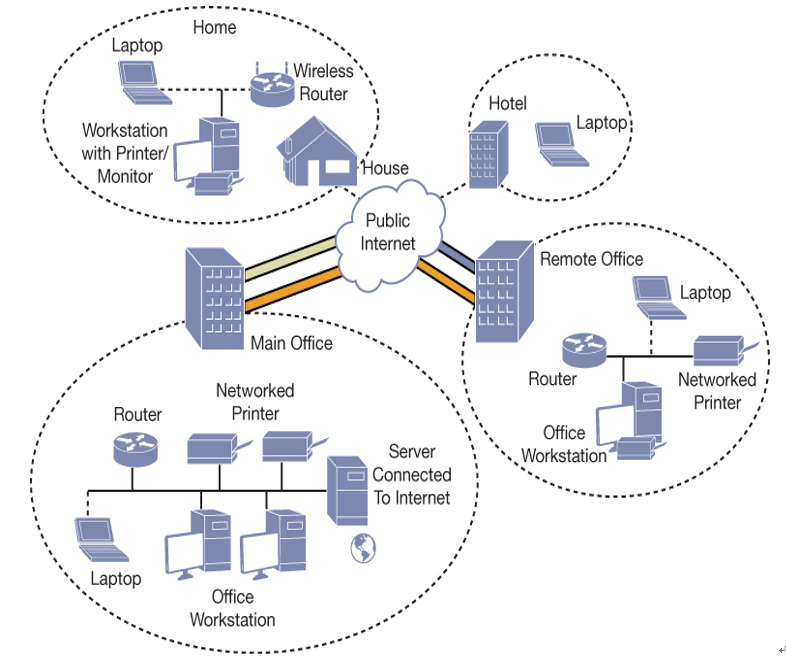
Figure 1-21 Using a VPN to connect locations securely over the internet
VPN protocols
Windows 10 supports four commonly used VPN protocols. Each protocol offers different characteristics:
- Point-to-Point Tunneling Protocol (PPTP) The oldest and what is considered one of the least secure of all supported VPN protocols. However, it can be used successfully in low-security scenarios because it is very easy to set up and still offers more protection than using PPP over the internet. PPTP creates the tunnel and then can use several authentication methods, including the Microsoft Challenge Handshake Authentication Protocol versions 1 and 2 (MS-CHAP v1 and MS-CHAP v2), Extensible Authentication Protocol (EAP), and Protected Extensible Authentication Protocol (PEAP). If EAP is used, certificates can be used with PPTP; otherwise, they are not necessary.
- Layer 2 Tunneling Protocol (L2TP) This protocol uses the IP security extensions (IPsec) for encryption and encapsulation. L2TP encapsulates the messages with IPsec, and then encrypts the contents using the Data Encryption Standard (DES) or Triple DES (3DES) algorithm. The encryption keys are provided by IPsec using Internet Key Exchange (IKE). L2TP/IPsec can use pre-shared keys or certificates for authentication. Using a pre-shared key is useful during testing and evaluation, but should be replaced with a certificate in a production environment.
- Secure Socket Tunneling Protocol (SSTP) This protocol encapsulates PPP traffic using the Secure Sockets Layer (SSL) protocol, which is widely supported on the internet and passes through TCP port 443, which is the same as SSL. Using the Extensible Authentication Protocol-Transport Layer Security (EAP-TLS) authentication protocol together with certificates makes SSTP a very versatile and widely used protocol.
- Internet Key Exchange, Version 2 (IKEv2) IKEv2 is most useful for mobile users and is the default protocol for Windows 10 when trying to connect to remote access servers. This protocol supports IPv6 traffic and the IKEv2 Mobility and Multi-homing (MOBIKE) protocol through the Windows VPN Reconnect feature, which allows automatic reconnection if a VPN connection is lost. Authentication is provided by using EAP, PEAP, EAP-MSCHAPv2, and smart cards. IKEv2 will not support older authentication methods, such as Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP), which offer low protection.

