Create, validate, and assign deployment profiles
You use Deployment Profiles to customize the OOBE for a device or group of devices when using Windows Autopilot. You can create a single default deployment profile of settings for your whole organization, or you can create additional deployment profiles and assign them to device groups.
New functionality has been added to Windows Autopilot with each release of Windows, and this is likely to continue. In Table 1-11, you can review how each version of Windows 10 since Version 1803 has introduced changes to how the Autopilot profile is downloaded.
TABLE 1-11 Windows Autopilot profile download
| Windows 10 version | Profile download behavior |
| 1803 | The Autopilot profile is downloaded as soon as possible. When using a wired connection, this is downloaded at the start of OOBE. If wireless, it is downloaded after the network connection page is displayed. |
| 1809 | The Autopilot profile is downloaded as soon as possible, and it is downloaded again after each reboot. |
| 1903 | White glove deployment added. Enables partners or IT support staff to pre-provision devices. Autopilot is now self-updating during OOBE. Sets the diagnostics data level to Full during OOBE. |
| 1909 | No specific improvements to Autopilot. |
| 2004 | Supports user-driven Hybrid Azure Active Directory join with VPN support (made available for 1903 and 1909). If the device is connected to Ethernet, language, locale, and keyboard pages are skipped in OOBE if configured in the profile. |
| 20H1 | Support for HoloLens deployments and for co-management. |
| 21H2 | Improvements to diagnostics collection and role-based access control for Autopilot administrators. |
Note Force Autopilot Profile to Be Downloaded
If a device has not downloaded an Autopilot profile, you should reboot the device during OOBE to allow the device to retrieve the profile. You can press Shift-F10 to open a command prompt at the start of the OOBE and then enter shutdown /r /t 0 to restart the device immediately, or enter shutdown /s /t 0 to shut down immediately.
At the time of this writing, the available profile settings that you can configure within a Windows Autopilot deployment profile are shown in Table 1-12.
TABLE 1-12 Windows Autopilot deployment profile settings
| Profile setting | Description |
| Convert All Targeted Devices To Autopilot | Enables you to register all targeted devices to Autopilot if not already registered. The next time registered devices go through the OOBE, they go through the assigned Autopilot scenario. |
| Deployment Mode | User-driven devices are devices that are associated with the user enrolling the device. Self-Deploying (preview) devices have no user affinity; an example is a kiosk device. If this setting is chosen, the following settings are enabled: Skip Work Or Home Usage SelectionSkip OEM Registration And OneDrive ConfigurationSkip User Authentication In OOBE |
| Join To Azure AD As | Azure AD–joined = Cloud-only Hybrid Azure AD–joined = Cloud and on-premises Windows Server Active Directory |
| Microsoft Software License Terms | This means that organizations accept the software license terms on behalf of their users. |
| Privacy Settings | Organizations can choose not to ask users about Microsoft-related privacy settings during the OOBE process. |
| Hide Change Account Options | Removes the option for users to restart the OOBE process with a different account. (Requires Windows 10 1809 or later.) |
| User Account Type | Typically, during the OOBE process, a device will automatically be set up with administrator access. This option can be disabled when using Windows Autopilot as you can choose a Standard or Administrator account type. |
| Allow White Glove OOBE | Enables a partner or IT pro to press the Windows key five times during OOBE to run without user authentication, enroll the device, and provision all system-context apps and settings. |
| Language (Region) | Enables you to select the appropriate regional settings. The keyboard is automatically selected based on this selection unless you choose otherwise. Defaults to Operating System default. |
| Automatically Configure Keyboard | If Yes, uses the regional selection to choose keyboard layout. |
| Apply Device Name Template | Allows you to specify a naming convention to automatically name devices. For example, Contoso-%RAND:3% will generate a device name such as Contoso-565. |
Note Company Branding is Required for Autopilot
You will notice that Autopilot profiles allow you to choose whether a user is presented with the company branding during OOBE. This setting is optional in each profile you create. Regardless of how you configure deployment profiles, you must configure Azure Active Directory Company Branding.
Use the following procedure to create a deployment profile using Microsoft Intune for a user-driven device that is to be joined to Azure AD:
- Open the Microsoft Endpoint Manager admin center and sign in as a global admin.
- Select Devices, select Enroll devices, and then select the Automatic Enrollment tile.
- Ensure the MDM user scope is not set to None.
- Go back to Enroll devices and select Deployment Profiles.
- Select Create profile and choose Windows PC.
- On the Create profile page, on the Basics tab, enter a profile name and optional description.
- Select Next, and then, on the Out-of-box experience (OOBE) tab, displayed in Figure 1-9, configure the values described in Table 1-12 and then select Next.
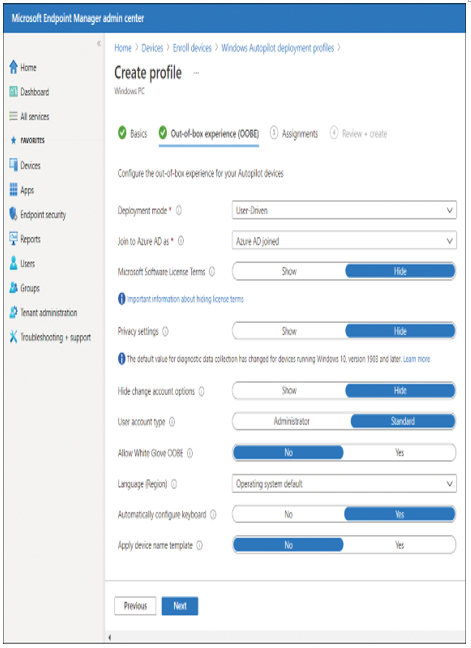
Figure 1-9 Creating an Autopilot profile
- On the Assignments page, choose the device groups you want to include or exclude, or choose Add all devices. Then select Next.
- On the Review + create tab, select Create.
After you’ve assigned the profile, devices are allocated to the profile during the Windows Autopilot process.