Configure Azure MFA – Deploy and upgrade operating systems
Configure Azure MFA
To enable Azure MFA for a single cloud-based Azure AD user, you must configure the MFA Service Settings. Then you can create a conditional access policy by using this procedure:
- Open the Azure Active Directory admin center (at https://aad.portal.azure.com) and sign in with a global administrator account.
- On the Overview blade, under Manage, select Users.
- On the menu bar, select Multi-Factor Authentication. A new browser windows opens.
- On the multi-factor authentication page, select the service settings tab.
- Under verification options, select all the boxes for Methods available to users (Call to phone, Text message to phone, Notification through mobile app, Verification code from mobile app or hardware token).
- Select Save.
Create a Conditional Access Policy for MFA
Once MFA settings have been configured, you need to assign them to users by creating a conditional access policy:
- In the Azure Active Directory admin center, under favorites, select Azure Active Directory.
- Select Security, and then select Conditional Access.
- Select New policy.
- On the Conditional Access Policy blade, provide a name for your policy.
- Under Assignments, select 0 users and groups selected.
- Choose between including and excluding specific users, groups, directory roles, and all guest and external users. For example, select Directory roles; then, in the drop-down list, select Global administrator.
Note Don’t Lock Yourself Out
Creating restrictive policies in conditional access for the global administrator account requires caution. Ensure you don’t configure settings that result in you locking yourself out.
- Under Cloud apps or actions, select the No cloud apps, actions, or authentication contexts selected link, and then choose the cloud apps or actions you want to protect with MFA. For example, select Microsoft Intune.
- Under Conditions, select the 0 conditions selected link, and configure the required settings. For example, select High and Medium Sign-in risk.
- Under Access controls, select the 0 controls selected link, ensure the Grant access radio button is selected, and select the check box for Require multi-factor authentication, as displayed in Figure 1-18.
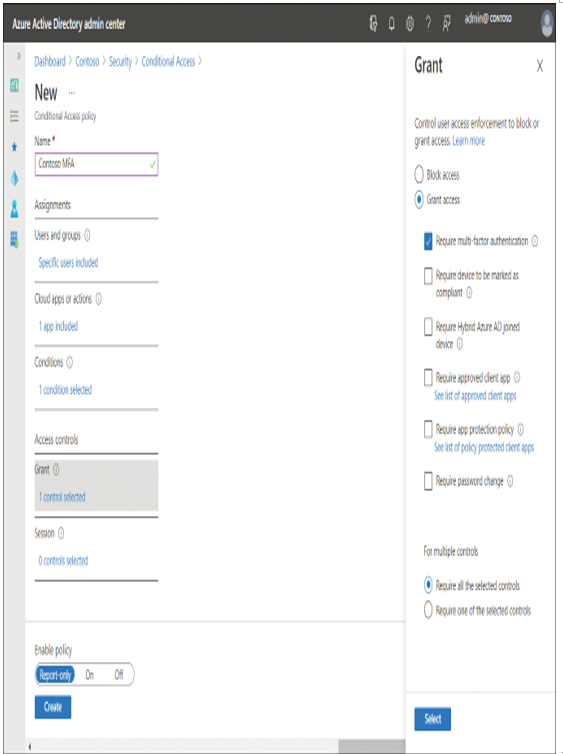
Figure 1-18 Creating a conditional access policy to require MFA
- Click Select.
- Under Enable policy, toggle the setting to On.
- Select Create.
- The policy is validated, and it appears in the Conditional Access Policies blade as Enabled.
After you have enabled Azure MFA, you can test it to ensure that the conditional access policy works. Test logging in to a resource, such as the Microsoft Endpoint Manager admin center, with a user who has MFA enabled, and verify that the user is required to provide additional authentication to access the resources.
Note Azure MFA For Administrators
Microsoft offers basic Azure MFA features to Office 365 and Azure AD administrators for no extra cost. All other users require Azure AD premium licensing.

