Configure Windows Hello and Windows Hello for Business
Windows Hello is a two-factor biometric authentication mechanism built into Windows 10. The personal biometric data created and used by Windows Hello is unique to the device on which it is set up, and it is not synced with other devices. Windows Hello allows users to unlock their devices by using facial recognition, fingerprint scanning, or a PIN.
Windows Hello for Business is the enterprise implementation of Windows Hello; it allows users to authenticate to Active Directory or Azure AD, and it enables users to access network resources. Administrators can configure Windows Hello for Business using Group Policy or by using mobile device management policy; it uses asymmetric (public/private key) or certificate-based authentication.
Windows Hello provides the following benefits:
- Strong passwords can be difficult to remember, and users often reuse passwords on multiple sites, which reduces security. Windows Hello allows them to authenticate using their biometric data.
- Passwords are vulnerable to replay attacks, and server breaches can expose password-based credentials.
- Passwords offer less security because users can inadvertently expose their passwords because of phishing attacks.
- Windows Hello helps protect against credential theft. Because a malicious person must have both the device and the biometric information or PIN, it becomes more difficult to hack the authentication process.
- Windows Hello can be used in cloud-only and hybrid-cloud deployment scenarios.
- Windows Hello logs you into your devices three times faster than by using a password.
To implement Windows Hello, your devices must be equipped with the appropriate hardware. For example, facial recognition requires that you use special cameras that see in infrared (IR) light. These can be external cameras or cameras incorporated into the device. The cameras can reliably tell the difference between a photograph or scan, and a living person. For fingerprint recognition, your devices must be equipped with fingerprint readers, which can be external or integrated into laptops or USB keyboards.
If you have previously experienced poor reliability from legacy fingerprint readers, you should review the current generation of sensors, which offer significantly better reliability and are less error prone.
After you have installed the necessary hardware devices, use these directions to set up Windows Hello:
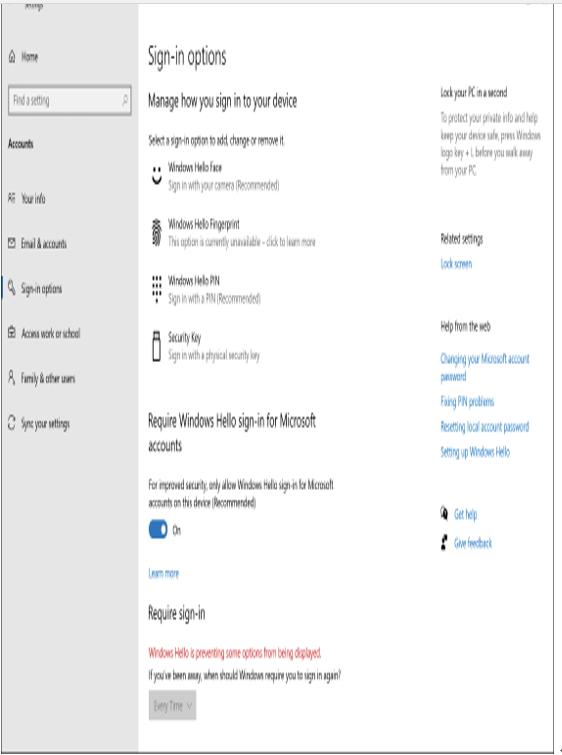
- Open the Settings app and select Accounts.
- On the Sign-in options page, under Manage how you sign in to your device, review the options for face or fingerprint. (If you do not have Windows Hello-supported hardware, the Windows Hello section does not appear on the Sign-in Options page.)
To configure Windows Hello, follow these steps:
- Under the Windows Hello section, select Windows Hello Face, and then select Set up.
- On the Welcome to Windows Hello page, select Get started.
- When prompted, enter your PIN or password to confirm your identity.
- Allow Windows Hello to capture your facial features, as shown in Figure 1-19.
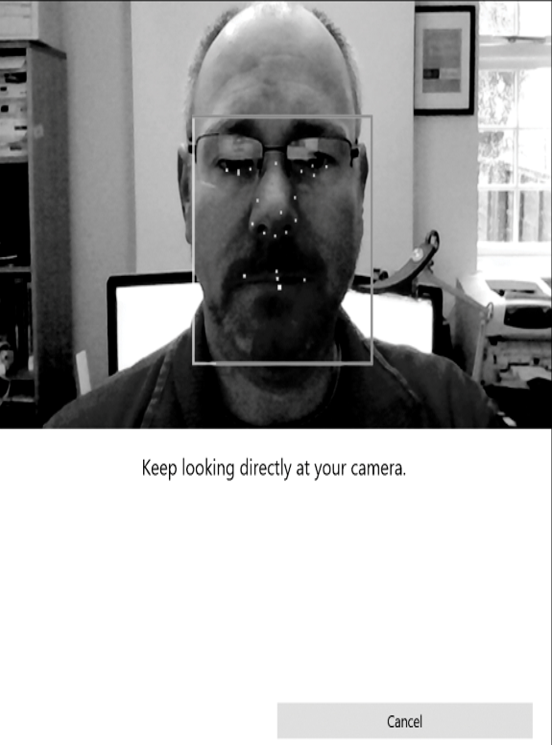
Figure 1-19 Configuring Windows Hello
5. Once complete, you are presented with an All Set! message that you can close.
Users can use Windows Hello for a convenient and secure sign-in method, which is tied to the device on which it is set up.
For enterprises who want to enable Windows Hello, they can configure and manage Windows Hello for Business. Windows Hello for Business uses key-based or certificate-based authentication for users by using Group Policy or by using a modern management approach, such as Microsoft Intune.
To manage Windows Hello for Business with Group Policy, you should review the two Windows Hello for Business GPO settings, which can be found in this node: User Configuration > Administrative Templates > Windows Components > Windows Hello for Business.
One setting is used to enable Windows Hello for Business, and the other setting is used to configure the use of certificates for on-premises authentication.
You also have additional Windows Hello for Business GPO settings available to manage your Windows Hello for Business deployment. These policies can be found in this node: Computer Configuration > Administrative Templates > Windows Components > Windows Hello for Business.
There are ten settings that allow you to configure hardware security devices, such as TPM. These settings also allow you to configure smart cards, biometrics settings, and more.
Need More Review? Windows Hello Biometrics in the Enterprise
To review further details about using Windows Hello in the enterprise, refer to the Microsoft website at https://docs.microsoft.com/windows/access-protection/hello-for-business/hello-biometrics-in-enterprise.