Manage application and driver deployment
You can use MDT to deploy and manage apps and drivers. To add applications, use the following procedure:
- In your deployment share, select and then right-click Applications.
- Select New Application.
- Complete the New Application Wizard by entering the following information:
- Choose between Application with source files, Application without source files or elsewhere on the network, or Application bundle.
- The details for the app, including Publisher, Application Name, Version, and Language.
- The Source (where the files are for the app) and the Destination (the name by which the app is known).
- Any command-line details needed to install the app. For example, for XML Notepad, the command line would typically be xmlnotepad.msi /q.
Exam Tip
If you want to deploy many apps, consider using a Windows PowerShell script to accelerate the process. You’ll need to import the MicrosoftDeploymentToolkit module.
Installing drivers is pretty similar:
- Select and then right-click the Out-of-Box Drivers folder.
- Select Import Drivers.
- Specify the folder location for drivers you want to import.
Create and use task sequences
After you’ve added all the required images, apps, and drivers, you must create task sequences to apply these to target computers. Task sequences are the collection of actions performed to complete a specific job, such as deploy Windows 10 and related apps to a target computer.
You use predefined templates to create your task sequences. Tasks typically include the following:
- Gather This task reads required configuration information from a deployment server.
- Format and Partition This task prepares the target hard disk for the operating system you’re deploying.
- Inject Drivers This task obtains the required drivers for a target computer and downloads them from a driver repository.
- Apply Operating System This task deploys the appropriate operating system image.
- Windows Update This task connects to a WSUS server and retrieves updates to apply to the target computer.
To create a task sequence, use the following procedure:
- In your deployment share, select and then right-click Task Sequences.
- Select New Task Sequence.
- Complete the New Task Sequence Wizard by entering the following information:
- A Task sequence ID and Task sequence name. These identify the task sequence, and together with optional Task sequence comments, are displayed by the deployment wizard during deployment.
- Choose a template. You can choose between Sysprep and Capture, Standard Client Task Sequence, Standard Client Upgrade Task Sequence, Post OS Installation Task Sequence, and many others.
- Choose the Operating Systems image.
- If necessary, enter a product key.
- Enter a user Full Name, Organization, web browser home page, and local administrator account password.
After you’ve created the task sequence, you’ll need to configure its settings. The procedure will vary based on what the task sequence does. But for example, to complete the process of configuring an operating system deployment task sequence, use the following procedure:
- In your deployment share, in the Task Sequences folder, right-click your task sequence and select Properties.
- Select the Task Sequence tab, displayed in Figure 1-13.
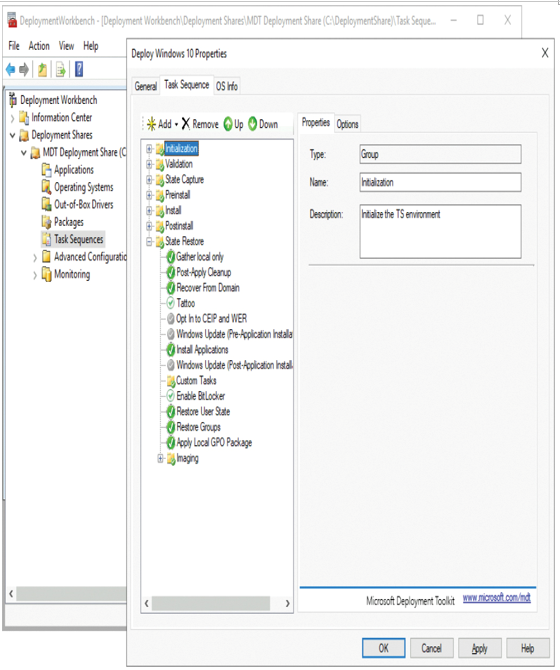
Figure 1-13 Reviewing the task sequence details
3. Verify and modify any required settings.
The final step before deployment is to configure the deployment share properties and related Windows PE settings. Use the following procedure:
- Right-click your deployment share and select Properties.
- On the General tab, verify the Platforms Supported (x86 and x64).
- Optionally, select the Enable multicast for this deployment share check box. This is only available if you’ve deployed a Windows Deployment Services role in your environment.
- On the Rules tab, review the contents of the displayed CustomSettings.ini file. These were defined in the initial task sequence creation.
- On the Windows PE tab, review the settings for creating a Windows PE boot disk. Remember to review the settings for your platform by selecting either x86 or x64 in the Platform list.
- On the Windows PE tab, beneath the Platform list, select the Features tab and review and revise required settings. These options determine additional features.
- Select OK, and if you made any changes, right-click your deployment share and select Update Deployment Share. Complete the wizard to refresh the settings in your deployment share.